
All In One WP Security & Firewall Tutorial 2021
[ad_1]
Firewall
Hover your mouse to WP Security tab and click Firewall.
Basic Firewall Rules Tab
All In One WP Security & Firewall Basic Firewall Rules feature allows you to enable basic firewall protection to your site. This’s one of the basic features you should enable from your site thus this will not affect your site’s overall functionalities.
From Basic Firewall Settings section, check Enable Basic Firewall Protection. Basic Firewall Protection will implement the following:
- Secure your .htaccess file by denying access to it.
- Disable the server signature.
- Set limit of file upload size to 10MB only.
- Secure your wp-config.php file by denying access to it.

Enable Basic Firewall Protection
Next, scroll to WordPress XMLRPC & Pingback Vulnerability Protection section, check Completely Block Access To XMLRPC to completely block external access to XMLRPC.
Why should we disable XMLRPC?
XMLRPC is a built-in feature of WordPress. It is a PHP file (xmlrpc.php) residing inside of WordPress that enables data transmission through HTTP with XML as the encoding mechanism. It simply enables remote access to your site. If you’re outside and you don’t have your computer, you could still access your site through your phone because of this feature. Wouldn’t that be helpful? Yes, that would be very helpful but XMLRPC feature has some serious security vulnerabilities. Leaving XMLRPC enabled makes your site prone to Brute Force Attack. Another security hole of XMLRPC is DDOS Attack, making your network resource unavailable, in short, taking your site offline.
XMLRPC vulnerabilities make the feature itself a security hole instead of a solution. You should justify XMLRPC’s upside and downside and only enable XMLRPC if you understand the risk of having it activated.
Here we’ll check Completely Block Access To XMLRPC to totally block external access to XMLRPC. We will also check Disable Pingback Functionality From XMLRPC in case there’s a need for us to use Jetpack or WP iOS or other apps that need WP XML-RPC feature. Disabling pingback functionality from XMLRPC will protect your site from WordPress pingback vulnerabilities. Click the button Save Basic Firewall Settings to save your changes.

WordPress XMLRPC & Pingback Vulnerability Protection
Additional Firewall Rules Tab
Listing Of Directory Contents
Check Disable Index Views feature. Why we should disable index views on our site? Let’s say you have created a folder inside of your site root directory and you forgot to create an index file inside of it. When you access that folder from your browser, you will only see a list of folders and files. If an expert on the web saw your directory listing, it is easy for them to determine which framework your site is using. Disabling the listing of directory contents doesn’t really make your site more secure but at least it will not list your folder and files in a single request.
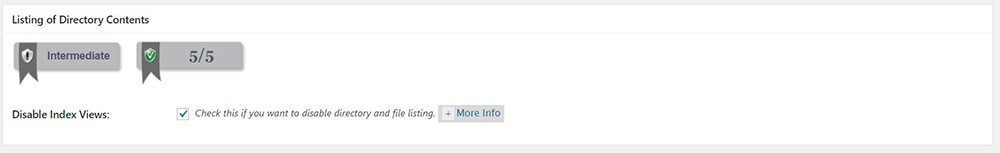
Disable Index Views
Trace and Track
Check Disable Trace and Track feature. HTTP Trace/Cross-site tracing (XST) is a form of Cross-site scripting (XSS) attack that is known for its capability to get HTTP header information (including cookies) of web users. We shouldn’t belittle this old type of attack thus it is still effective in stealing the victim’s web credentials.
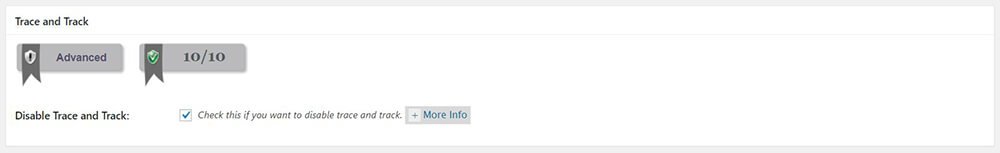
Disable Trace and Track
Proxy Comment Posting
Enable Forbid Proxy Comment Posting. This feature will deny any requests from a proxy server when posting comments. Spammers commonly use a proxy server when they make spam or spambots. Why? The proxy server simply hides their real IP address. It encrypts their data before it sends a request to your web server and still, your web server will return the correct response. The proxy server itself isn’t bad or harmful in its way thus people use it to control their network. They use it to save bandwidth and improve internet speed, setup security, and many more. Still, proxy server is the most fitted machine for intruders to create spam. By enabling Forbid Proxy Comment Posting, you’re eliminating some spam and other proxy requests.
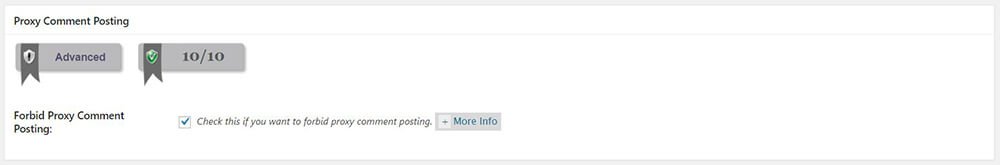
Forbid Proxy Comment Posting
Bad Query Strings
Enable Deny Bad Query Strings feature. When navigating to your site, you will notice that sometimes your URL contains a query string (ex. http://www.yoursite.com/contact?query=foo&query2=). With that kind of URL format, an attacker could just change the query string or change the query value. An attacker could perform an XSS attack if you don’t properly use your query. Other WordPress plugins use query string so make sure they properly sanitize query values. Enabling Deny Bad Query Strings to give your site protection against malicious queries via XSS.
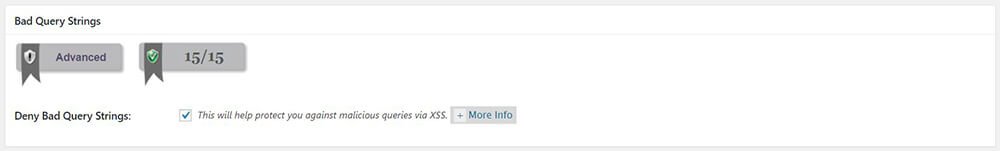
Deny Bad Query Strings
Advanced Character String Filter
Check Enable Advanced Character String Filter feature. This feature will protect your site from malicious string attacks coming from XSS. Advanced Character String Filter will simply detect malicious string patterns and will return a 403 error for the attacker attempting an XSS attack.

Enable Advanced Character String Filter
[ad_2]
Source link
